If you have spent time following our project, you already know what we are all about. At the heart of Serenity Shield’s core ethos lies a profound belief: we must regard data sovereignty as a fundamental human right, not simply a luxury in this digital age. In this rapidly evolving digital age, we believe that controlling one’s data will soon emerge as a recognized necessity for modern digital society.
Today, we detract from our usual discourse by sharing a ground-level story from one of our teammates. This tale underscores the urgency of our mission precisely because it hit so close to home.
Navigating the Digital Landscape
We find ourselves at the forefront of an enduring digital battle—a conflict that will persist as long as humanity continues integrating technology into daily life’s fabric. Through vigilance, education, and innovation, we aspire to protect ourselves and our community from the lurking dangers of the digital realm.
This narrative serves not as a mere update. It serves as a humbling testament to the ever-present digital risks that loom large in this digital era. Our unwavering commitment to transparency and education drives us to share this story. While the incident proved humbling, it nevertheless provides both an object lesson and a cautionary tale of the pervasive risks we all face as we progress further into the digital era. Allow me to set the scene for you.
A Digital Misstep
Our story unfolds against the backdrop of a then-upcoming AMA with our community on Twitter Spaces. Nikos, our Head of Marketing, was prepping for the event. Our team relishes these events because they enable us to interact directly with people with a vested interest in the problems we aim to solve. It allows us to talk with people who understand the importance of what we do. These sessions are not just about dialogue—they enable the team to connect with those who resonate with our mission.
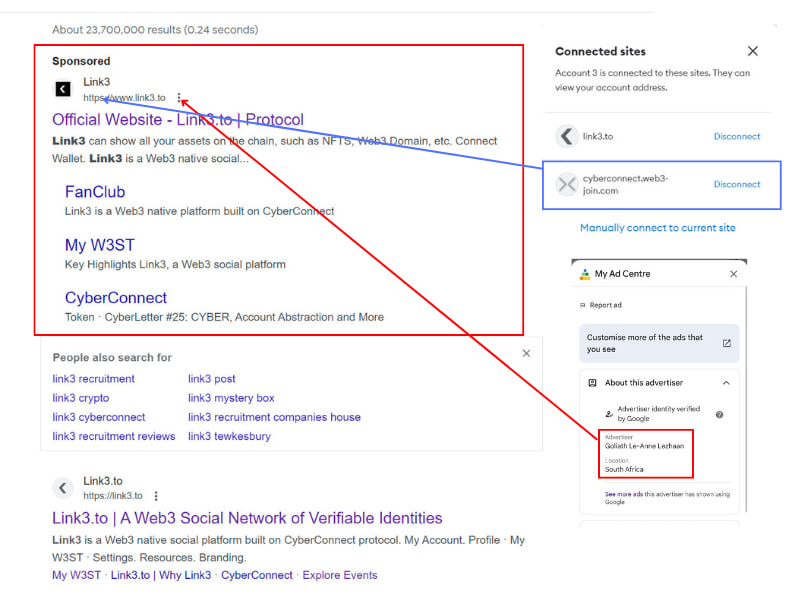
As a customary gesture of gratitude for attending AMAs, we typically reward our loyal community members for their support and participation. In line with this tradition, Nikos was set to distribute these rewards via a funded treasury account on Link3 – the world’s largest Web 3 AMA social media platform. However, when he logged into Metamask to initiate the reward transfers, he was met with an unsettling revelation: someone had inexplicably and unexpectedly emptied the digital wallet of funds.
The scam was deceptively simple. Nikos, intending to transfer funds to a perfectly reputable vendor, clicked on what seemed to be a legitimate link. In reality, it was a fraudulent sponsored ad on Google — a trap leading to a cloned site.
A Humbling Experience
Let us spell out the scam clearly. Nikos intended to pay one of our vendors out of the wallet. When Nikos googled our vendor, he clicked on the first link that appeared, assuming it was legitimate. In reality, the link that populated in his search – as a Sponsored Ad, no less – directed traffic to a clone site to trick people into interacting with a fraudulent address.
Sites that require someone to sign in using their digital wallet often require confirmation on chain in the form of a digital transaction. Therefore, he was not surprised when he was prompted to confirm the transaction. That was all it took for us to get scammed.
Unravelling the Mystery
Now that we have covered what happened, let us circle back to the AMA preparation. Despite the setback, the professional Nikos refused to allow this incident to overshadow the AMA. The AMA went off without a hitch, and we had a great time. Behind the scenes, however, Nikos feverishly worked at piecing together what had transpired.
Following the AMA, Nikos meticulously reviewed the wallet transactions, trying to pinpoint the breach. With the support of our technical team, he traced the breach back to the previous 48 hours. This makes a lot of sense. Generally, once a wallet has become compromised, the bad actors tend not to waste much time dilly-dallying. They identify a vulnerability, attack, and then disappear, taking as much with them as possible.
Luckily for us, the answer dawned on him quickly. His epiphany came when he recalled a transaction prompt from our vendor’s portal. He recalled being prompted for a transaction when interacting with our vendor. Nikos had attempted to connect with their portal, which requires a wallet with which to sign in.
It was here that the trap was sprung. While he swiftly secured the wallet by revoking permissions, the damage had already been done. The funds were gone. To add further insult to injury, the malicious ad remains live as of this writing despite being reported to Google.
Reflections from the Digital Trenches
Put yourself in Nikos’ shoes momentarily—a seasoned digital veteran blindsided by this scam. This incident is a chilling reminder: if it can happen to an experienced individual, what hope does a digital novice have? This incident is more than just a story — it provides a testament to our digital adversaries’ deep cunning and constantly evolving tactics. Furthermore, it illustrates the vulnerability of even the most experienced user.
Despite everything, within this challenge lies an opportunity. It reinforces our mission and our unwavering commitment. It serves as a clarion call for us, underscoring the importance of data sovereignty, security, and the foundational principles for which Serenity Shield advocates. No one is safe at the moment, not even us.
Embracing the Future of Privacy with Serenity Shield
Incidents like the one Nikos endured underscore the importance of Serenity Shield’s commitment to privacy and data protection. Our approach ensures that personal data remains confidential and secure, giving users peace of mind and control over their information.
As the world wrestles with the complexities of evolving scams and bad actors, Serenity Shield will remain unwavering in its commitment to our users. With an emphasis on transparency, security, and user empowerment, we will lead from the front, developing innovative solutions that protect personal data to usher in the new era of privacy and confidentiality we desperately need.
The Next Step – Join Us
Join us on this transformative journey towards a more secure and private digital world. Together, we can redefine privacy and protect what is most valuable – your digital life.
For more information, please also join us on our Telegram channel. There, you will be the first to know about official project announcements and developments. Additionally, you can also find us on Twitter, Discord, and our website. Please visit our whitepaper and previous articles here for a more in-depth discussion of our project. We are always available on all of our platforms to assist with your questions.

Leave a Reply